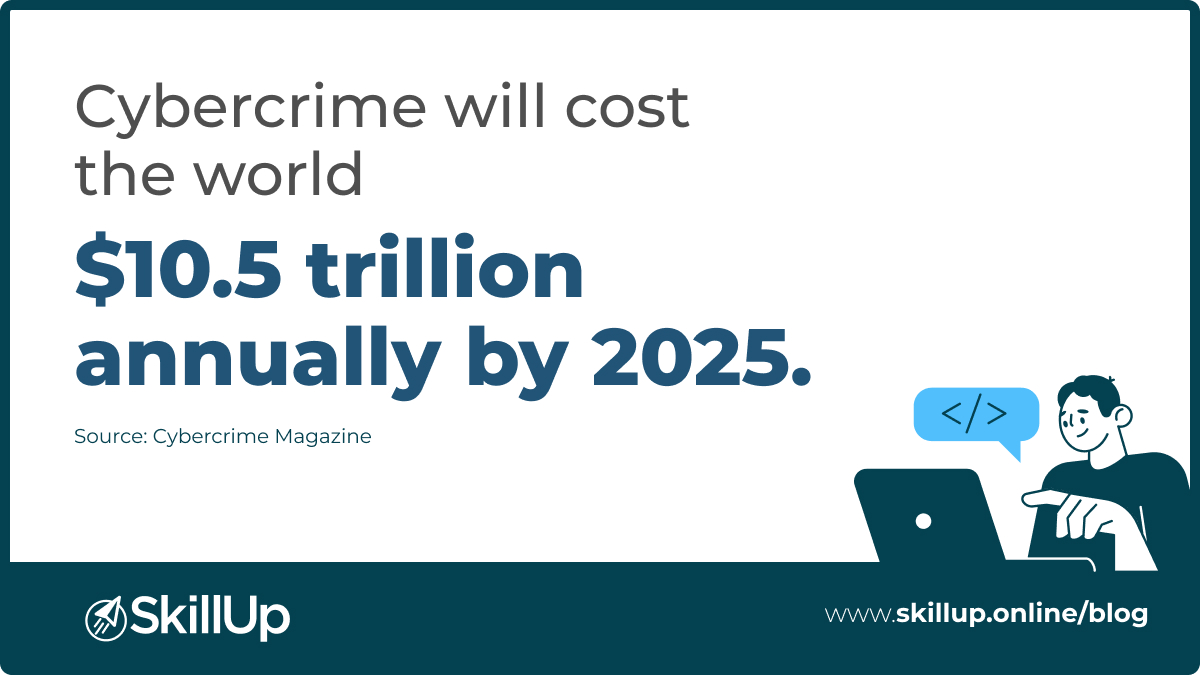
Introduction
In today’s digitally connected world, everything from our finances to our social lives has shifted online, and the need for robust cybersecurity has never been more critical. Cyber threats are like invisible adversaries constantly lurking in the digital shadows, waiting for the perfect moment to strike. They can disrupt businesses, steal sensitive information, and even compromise our personal privacy. And as the demand for cybersecurity grows, so do the opportunities for those who want to make a career out of defending the digital realm.
So, whether you’re a tech enthusiast, a business owner safeguarding sensitive data, or simply someone who values their digital identity, this guide will help you understand cybersecurity from scratch.
What is Cybersecurity?
Cybersecurity is the practice of safeguarding computer systems, networks, and data from unauthorized access and malicious attacks. In a world where cyber threats continually evolve, its importance cannot be overstated. By implementing robust cybersecurity measures, organizations and individuals can protect their assets, maintain data integrity, and ensure continuous availability of services.
The CIA Triad
This essential trio forms the cornerstone of information security and understanding it will help fortify your digital world with a sense of confidence and responsibility.
- Confidentiality: Imagine your digital assets are precious secrets locked away in a secure vault accessible only to trusted individuals. Confidentiality ensures that sensitive data remains confidential and is disclosed only to authorized parties. This principle shields your information from unauthorized access, safeguarding it from potential threats.
- Integrity: Just like ensuring the authenticity of a valuable artefact, integrity safeguards the accuracy and consistency of your data. It ensures that your digital assets remain unaltered, trustworthy, and free from unauthorized modifications. With integrity, you can have confidence in the authenticity and reliability of your digital world.
- Availability: Think of your favorite online services always being accessible whenever you need them, like a dependable assistant. Availability ensures that your data, services, and resources are available to authorized users when required. It safeguards against disruptions and ensures seamless functionality.
Specialties in Cybersecurity
As you venture further into the realm of cybersecurity, you’ll discover an array of specialized roles, each contributing uniquely to the protection of digital assets. Let’s explore some of these key specialties.
- Network Security: The Guardian of Networks specializes in securing communication channels and infrastructure. They set up safeguards to prevent unauthorized access and protect data as it travels across networks.
- Application Security: The App Defender focuses on fortifying software applications to withstand cyber threats. They identify and address vulnerabilities, ensuring that applications remain secure and resilient.
- Cloud Security: The Cloud Protector ensures the safety of data stored in the cloud. This expert implements measures to safeguard information and control access to cloud-based resources.
- Incident Response: When a cyber-crisis strikes, the Incident Responder comes to the rescue. They swiftly handle security incidents, mitigating the impact and restoring normalcy.
- Threat Hunting: The Cyber Detective is a skilled professional who proactively searches for hidden threats and vulnerabilities, taking pre-emptive action to counter potential cyberattacks.
- Ethical Hacking/Penetration Testing: Ethical Hackers and Penetration Testers put on their detective hats to uncover weaknesses in systems and applications. By responsibly exploiting vulnerabilities, they help organizations strengthen their defences.
- Cybersecurity Management: The Mastermind oversees it all. Cybersecurity managers strategize and lead security efforts, ensuring a cohesive defence and alignment with business objectives.
These specialists form a robust cybersecurity team, working together to shield the digital world from harm.
Basic Terminologies
Understanding the fundamental terminologies of cybersecurity is essential for building a strong foundation in this domain. Let’s explore some key terms that you’ll frequently encounter in the world of cybersecurity.
- Malware: Short for “malicious software,” malware is any software designed to harm or exploit computer systems and networks. Common types of malware include viruses, worms, Trojans, and ransomware.
- Phishing: Phishing is a deceptive practice wherein cyber attackers use emails, messages, or websites to trick users into revealing sensitive information, such as login credentials or financial data.
- Firewall: A firewall is a security mechanism that acts as a barrier between a trusted internal network and untrusted external networks, monitoring and controlling incoming and outgoing traffic based on predefined rules.
- Encryption: Encryption is the process of converting data into a coded format to prevent unauthorized access. Only those with the appropriate decryption key can decipher the information.
- Authentication: Authentication is the process of verifying the identity of a user or entity, ensuring that only authorized individuals can access certain resources or systems.
- Vulnerability: A vulnerability is a weakness or flaw in a system’s design, configuration, or software that can be exploited by cyber attackers to gain unauthorized access or compromise data.
- Patch Management: Patch management involves regularly applying updates and fixes (patches) to software and systems to address known vulnerabilities and enhance security.
By familiarizing yourself with these basic terminologies, you’ll be better equipped to understand the various cybersecurity concepts and discussions you’ll encounter as you continue your journey in this field.
Common Types of Attack
In the ever-evolving landscape of cybersecurity, cyber attackers employ a wide array of tactics to breach defences and compromise systems. Let’s explore some common types of cyberattacks.
- Distributed Denial of Service (DDoS): In a DDoS attack, multiple compromised devices flood a target system with an overwhelming amount of traffic, causing it to become slow or unavailable to legitimate users.
- Ransomware: Ransomware is a type of malware that encrypts a victim’s files, rendering them inaccessible until a ransom is paid to the attacker to unlock the data.
- Man-in-the-Middle (MITM): In a MITM attack, the attacker intercepts and relays communications between two parties, often leading to the theft of sensitive information or unauthorized access.
- SQL Injection: SQL injection is a type of cyberattack that exploits vulnerabilities in a web application’s code to manipulate the backend database, potentially revealing or altering sensitive data.
- Social Engineering: Social engineering involves manipulating individuals into divulging confidential information or performing certain actions, often through psychological manipulation and deception.
- Zero-Day Exploits: Zero-day exploits target undisclosed vulnerabilities in software or systems before the developers can release a patch, making them particularly dangerous and difficult to defend against.
- Advanced Persistent Threats (APTs): APTs are sophisticated, targeted attacks that aim to infiltrate a specific target over an extended period, often carried out by well-funded and skilled threat actors.
Understanding these common attack types will help you recognize potential threats and reinforce your cybersecurity defences. By staying vigilant and informed, you’ll be better prepared to protect yourself and others from the ever-present dangers of the digital world.
Job Roles in Cybersecurity
In the dynamic field of cybersecurity, a wide range of specialized job roles offer exciting opportunities for aspiring professionals. Each role plays a critical part in defending against cyber threats and protecting valuable digital assets.
- Cybersecurity Analyst: As a cybersecurity analyst, you are at the forefront of safeguarding systems and networks. Your primary responsibility is to monitor security measures, detect potential vulnerabilities, and respond to security incidents swiftly. This role demands strong analytical skills and the ability to stay vigilant in identifying emerging threats.
- Security Engineer: Security engineers are the architects of cybersecurity defences. They design and implement security solutions, including firewalls, intrusion detection systems, and encryption protocols. This role requires a deep understanding of network and system security, along with the ability to design robust defences against evolving threats.
- Incident Response Specialist: When a cybersecurity incident occurs, the incident response specialist takes charge. Their mission is to investigate, contain, and mitigate the impact of security breaches. This role demands quick thinking, excellent problem-solving skills, and the ability to work under pressure.
- Penetration Tester/Ethical Hacker: As a penetration tester or ethical hacker, you emulate cyber attackers to identify vulnerabilities in systems and applications. Ethical hacking involves conducting authorized simulated attacks to help organizations strengthen their security measures.
- Chief Information Security Officer (CISO): The CISO is a top-level executive responsible for establishing and managing an organization’s overall cybersecurity strategy. This role involves aligning cybersecurity initiatives with business objectives, overseeing security operations, and addressing compliance issues.
- Security Consultant: Security consultants provide expert guidance to organizations on cybersecurity best practices. They conduct risk assessments, develop security policies, and offer tailored recommendations to enhance an organization’s security posture.
- Information Security Auditor: Information security auditors assess the effectiveness of an organization’s security controls and practices. They conduct audits, evaluate vulnerabilities, and ensure compliance with industry regulations and standards.
- Malware Analyst/Reverse Engineer: Malware analysts specialize in dissecting and understanding malicious software. Their expertise helps in developing effective strategies to detect and mitigate malware threats.
- Cryptographer: Cryptographers focus on designing and analysing cryptographic algorithms and protocols. Their work is critical in safeguarding data confidentiality and integrity.
- Cloud Security Specialist: With the rise of cloud computing, cloud security specialists focus on securing cloud-based infrastructure and services. They ensure that data stored and processed in the cloud remains protected from unauthorized access. If your interests lie within the cloud security domain, it might be worth mapping out a cloud security career path for yourself.
Cybersecurity Certifications
Obtaining cybersecurity certifications can significantly boost your credibility and open doors to exciting career prospects. Let’s explore some widely recognized certifications in the cybersecurity domain.
- CompTIA Security+: This entry-level certification covers essential cybersecurity principles, including risk management, network security, and cryptography. It’s an excellent starting point for beginners.
- Certified Information Systems Security Professional (CISSP): The CISSP certification is ideal for experienced professionals seeking to focus on various domains, such as security and risk management, asset security, and communication security.
- Certified Ethical Hacker (CEH): As a CEH, you’ll learn ethical hacking techniques to identify vulnerabilities and protect against cyber threats. This certification is ideal for those interested in penetration testing.
- Certified Incident Handler (GCIH): The GCIH certification validates your skills in incident response and handling cybersecurity incidents effectively.
- Certified Information Security Manager (CISM): Aimed at IT professionals and managers, the CISM certification focuses on governance, risk management, and information security program management.
- Specific Technology Specialization: For those preferring to focus on Microsoft technologies, Microsoft has several certifications such as the you could learn. You can also take relevant Microsoft exams and pass them to become a certified cybersecurity professional.
These certifications demonstrate your expertise and dedication to the cybersecurity field, making you a valuable asset to organizations seeking skilled professionals. Remember, continuous learning and staying up to date with the latest industry trends will pave the way for a successful and rewarding career in cybersecurity. So it’s always good to explore the possible learning paths in cybersecurity that you can take and chose the one that you want to specialize in.
Building a Career in Cybersecurity
Embarking on a career in cybersecurity opens doors to a thrilling and ever-evolving realm where you’ll play a crucial role in defending against cyber threats and protecting digital assets. To build a successful career in this domain, it’s essential to adopt a strategic approach, cultivate valuable skills, and stay dedicated to continuous learning.
Let’s explore some essential steps that will guide you along this exciting path.
- Educational Background and Skillset
A solid educational foundation is key to launching your cybersecurity journey. Consider pursuing a degree in computer science, information technology, or cybersecurity. Such programs will equip you with a comprehensive understanding of computer systems, networks, and cybersecurity principles.
Also, develop critical technical skills in programming languages such as Python, C++, or Java, as they are valuable assets in understanding security vulnerabilities and writing secure code. Networking knowledge is equally crucial, as it forms the backbone of communication systems, and understanding network protocols will help you analyze network security.
Plus, hone your problem-solving skills and analytical thinking. Cybersecurity professionals face complex challenges, and your ability to analyze incidents and devise effective solutions will be highly valuable.
- Gain Hands-on Experience
Seek internships or part-time jobs in cybersecurity-related roles, as they provide practical exposure to real-world scenarios. Look for opportunities with companies, government agencies, or cybersecurity consulting firms.
Additionally, it’s good to participate in capture-the-flag (CTF) competitions and cybersecurity challenges. These simulated scenarios enable you to apply your knowledge in a fun and competitive environment. They also improve your problem-solving skills and offer a glimpse into various cybersecurity domains.
Contributing to open-source projects can also be a valuable experience. It allows you to collaborate with experienced professionals, understand how security features are implemented, and contribute to the cybersecurity community.
- Networking and Professional Development
In the world of cybersecurity, networking is more than just connecting devices; it’s about building meaningful connections with industry professionals. So, engage with cybersecurity communities through online forums, social media groups, and professional networking platforms. Participate in discussions, share your knowledge, and seek guidance from experienced practitioners.
It’s also good to attend cybersecurity conferences and local meetups to gain insights into the latest trends, technologies, and best practices. These events provide opportunities to meet potential mentors and employers.
Plus, consider pursuing cybersecurity certifications like CompTIA Security+, Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and others to elevate your professional standing.
- Staying Updated with Industry Trends
Cybersecurity is a rapidly evolving field, so stay updated with the latest industry trends, news, and research. Follow cybersecurity blogs, subscribe to industry newsletters, and attend webinars to expand your knowledge.
Also, engage with thought leaders on social media platforms to gain insights from their expertise. By staying informed about the ever-changing cybersecurity landscape, you’ll be better prepared to adapt to new challenges and make informed decisions throughout your career.
Building a successful career in cybersecurity requires a blend of education, practical experience, networking, and continuous learning. As you progress along this journey, remember that the cybersecurity community is supportive and collaborative. Embracing challenges, staying curious, and committed to ethical practices is crucial, and your passion for securing the digital world will propel you toward becoming a valuable and respected cybersecurity professional.
Protecting Yourself from Cyber Threats
As you delve deeper into the cybersecurity world, it’s essential to protect your own digital life. Here are some practical tips to safeguard yourself from cyber threats.
- Use Strong Passwords and Multi-Factor Authentication: Use strong, unique passwords for each online account. Enable multi-factor authentication (MFA) whenever possible to add an extra layer of security.
- Keep Software and Devices Updated: Regularly update your software, operating systems, and devices to patch known vulnerabilities and protect against exploits.
- Avoid Phishing Scams: Be cautious with emails, messages, or links from unknown sources. Verify the sender’s authenticity before clicking on any links or providing sensitive information.
- Be Cautious with Personal Information Online: Limit the amount of personal information shared on social media and other platforms. Cybercriminals can use such data for identity theft and other malicious purposes.
- Use Secure Wi-Fi Connections: Avoid using public Wi-Fi networks for sensitive tasks. If you must connect to a public network, use a virtual private network (VPN) for added security.
You can further look up the 3 IT skills that are essential to keep security threats at bay to improve your threat readiness.
Cybersecurity Best Practices for Businesses
As a serious player in the cybersecurity landscape, businesses must prioritize robust security measures to protect their assets and customers. Here are some essential best practices.
- Increase Employee Training and Awareness: Educate employees about cybersecurity risks and best practices. Human error is a common cause of security breaches, and informed employees can be your first line of defence.
- Implement a Robust Firewall: Install and configure firewalls to monitor and control incoming and outgoing network traffic, and to protect your internal systems from external threats.
- Carry Out Regular Data Backups: Maintain regular backups of critical data. In the event of a cyber-incident, backups can help restore lost information and minimize downtime.
- Implement Access Control and Privileged Account Management: Limit access to sensitive data and systems only to authorized personnel. Implement strict access controls and regularly review privileged account permissions.
- Formulate Your Incident Response and Disaster Recovery Planning: Develop comprehensive incident response and disaster recovery plans to handle cybersecurity incidents effectively and minimize their impact.
By adhering to these best practices, businesses can create a resilient cybersecurity posture and mitigate potential risks effectively.
As you continue your journey in the world of cybersecurity, remember that diligence, continuous learning, and a commitment to ethical practices are the hallmarks of a true cybersecurity professional. Embrace the challenges, stay curious, and be a force for positive change in the realm of digital security.
Emerging Trends in Cybersecurity
In the dynamic landscape of cybersecurity, innovative technologies and trends are continually shaping the way we defend against cyber threats. Here are some exciting emerging trends to keep an eye on:
- Artificial Intelligence in Cybersecurity: AI and machine learning are transforming cybersecurity by enhancing threat detection, automating incident response, and enabling adaptive defences that evolve in real-time.
- Internet of Things (IoT) Security: As IoT devices become more prevalent, securing them becomes crucial. IoT security focuses on protecting interconnected smart devices to prevent potential breaches and data leaks.
- Blockchain Technology and Cybersecurity: Blockchain’s decentralized and immutable nature offers exciting possibilities for secure authentication, data integrity, and protecting digital transactions.
- Biometric Authentication: Biometrics, such as fingerprint and facial recognition, provide robust identity verification methods, reducing reliance on traditional passwords.
- Cloud Security Advancements: Cloud security solutions are evolving to address the unique challenges of cloud-based environments, ensuring data protection and compliance.
Exploring these emerging trends will broaden your understanding of the future of cybersecurity and prepare you to embrace cutting-edge technologies in your cybersecurity journey.
Your Next Steps
As you can see, the journey in the realm of cybersecurity offers plenty of career opportunities and growth. It’s also important to remember that cybersecurity is not just about protecting data and systems but also safeguarding the digital world and making a positive impact on individuals, businesses, and society as a whole. And with the help of online professional courses and programs, you can build these requisite skills and transform into a successful cybersecurity professional.
So, stay curious, keep learning, and remain vigilant against cyber threats. Embrace the challenges and be a proactive agent in defending against ever-evolving cyber risks.
If you would like to know more about how you can build skills and get started as a cybersecurity professional, contact our Learner Support Team at [email protected]. They will be more than happy to guide you on the next steps you can take.
SkillUp Online